OT Security
NAONWORKS OT Security Framework
Perfect from connection to protection
This seamless combination of solutions for OT environments
protects your ciritical systems from evolving security threats.

OT Security Issues: Exploring the Causes
- done Increase of connectivity between OT and IT networks
-
 The occurrence of security threats through the connection between OT and IT network
The occurrence of security threats through the connection between OT and IT network
- done Environmental vulnerabilities for security threats
-
 An outdated operating system, patch
An outdated operating system, patch
-
 Frequent use of file-sharing/remote access programs
Frequent use of file-sharing/remote access programs -
 Use of OT protocols vulnerable to security
Use of OT protocols vulnerable to security
- done The inadequate asset visibility specialized for OT environment
-
 Limitations in applying IT network security techniques to OT networks
Limitations in applying IT network security techniques to OT networks
-
 Advanced malware/ransomware targeting specific ICS
Advanced malware/ransomware targeting specific ICS
-
 Lack of security technologies based on OT protocol analysis
Lack of security technologies based on OT protocol analysis
- done Need for systematic management across OT and IT
-
 Inadequate network visibility and monitoring management
Inadequate network visibility and monitoring management
-
 A lack of investment in security threat detection and management
A lack of investment in security threat detection and management
-
 The absence of systematic and integrated security compliance
The absence of systematic and integrated security compliance
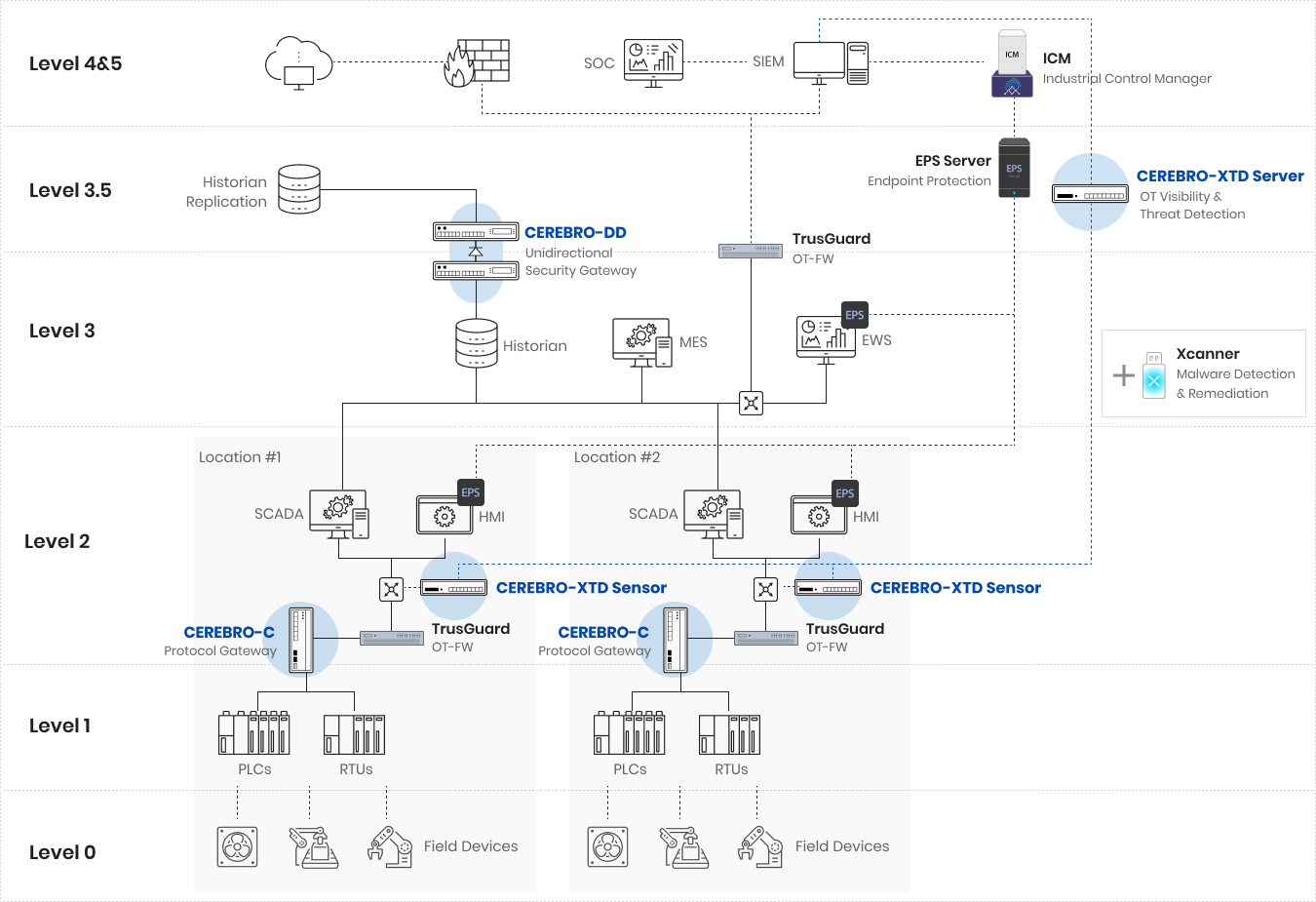
Matters to consider upon OT security construction
Security requirements that take into account the internal environment of the OT network must be fulfilled. The availability of facilities must be guaranteed, and the analysis of various OT protocols must support visibility, data transmission, and security threat detection.

-
OT
Security

-
Visibility
asset and network identification & Monitoring

-
Unidirectional GW
data diode for secure data transmission

-
Threat Detection
malicious code & anomalies
vulnerabilities

-
Segmentation
network separation &
network perimeter security

-
OT Protocol DPI
function, address, value analysis
-
ACL
unauthorized IP
function code control
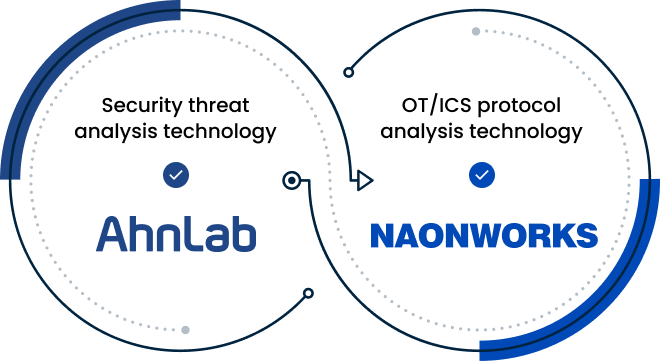
The security strategies and framework
with AhnLab
NAONWORKS and AhnLab offer OT security optimized for various customer environments
depending on security strategies per level of identification, detection, and response.
- Identification
- Detection
- Response

Endpoint
-
AhnLab EPS
Endpoint assets/process identification
AhnLab EPS
Malicious code inspection / Unauthorized process detection
AhnLab EPS
Whitelist control/Media control
AhnLab Xcanner
Non-resident malicious code inspection/removal

Network/Facility
-
AhnLab TrusGuard
Unauthorized traffic detection
AhnLab TrusGuard
Unauthorized traffic blocking


